SOC 2 COMPLIANCE AUDIT
SOC 2 COMPLIANCE AUDIT:
SOC 2 compliance is particularly relevant to service organizations that provide services such as cloud computing, data hosting, software as a service (SaaS), or any other services that involve the storage, processing, or transmission of customer data. The key factors audited in SOC 2 include
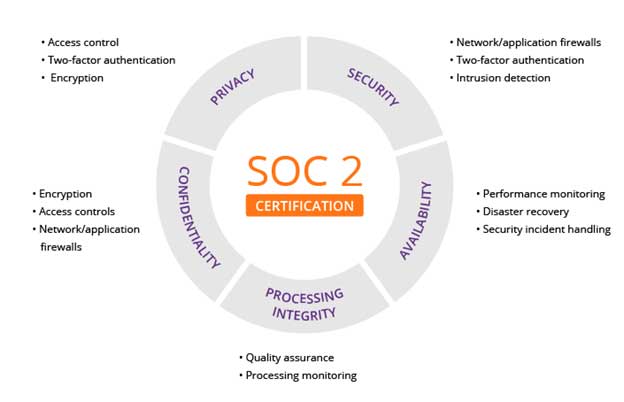

Security:
The auditor examines factors such as:Access controls and user management
Network security and firewalls
Data encryption and protection measures
Incident response and monitoring
Physical security of facilities
Availability:
The auditor examines factors such as:Redundancy and fault tolerance
Disaster recovery and business continuity planning
Downtime monitoring and response procedures
Performance and capacity management
Processing Integrity:
The auditor examines factors such as:Data validation and integrity checks
Error handling and correction procedures
Controls to prevent unauthorized or fraudulent transactions
Audit trails and data accuracy verification
Confidentiality:
The auditor examines factors such as:Data classification and access controls
Encryption of sensitive data
Non-disclosure agreements (NDAs) and confidentiality policies
Employee training on handling confidential information
Privacy:
The auditor examines factors such as:Privacy policy and notice to customers
Consent and data subject rights management
Data retention and deletion policies
Privacy incident response and breach notification procedures
