INCIDENT RESPONSE AND MALWARE ANALYSIS
INCIDENT RESPONSE AND MALWARE ANALYSIS:
Incident Response and Malware Analysis are two essential components of cybersecurity aimed at effectively detecting, containing, mitigating, and recovering from security incidents and malware infections. Both practices are critical for maintaining the security and integrity of IT systems and data.
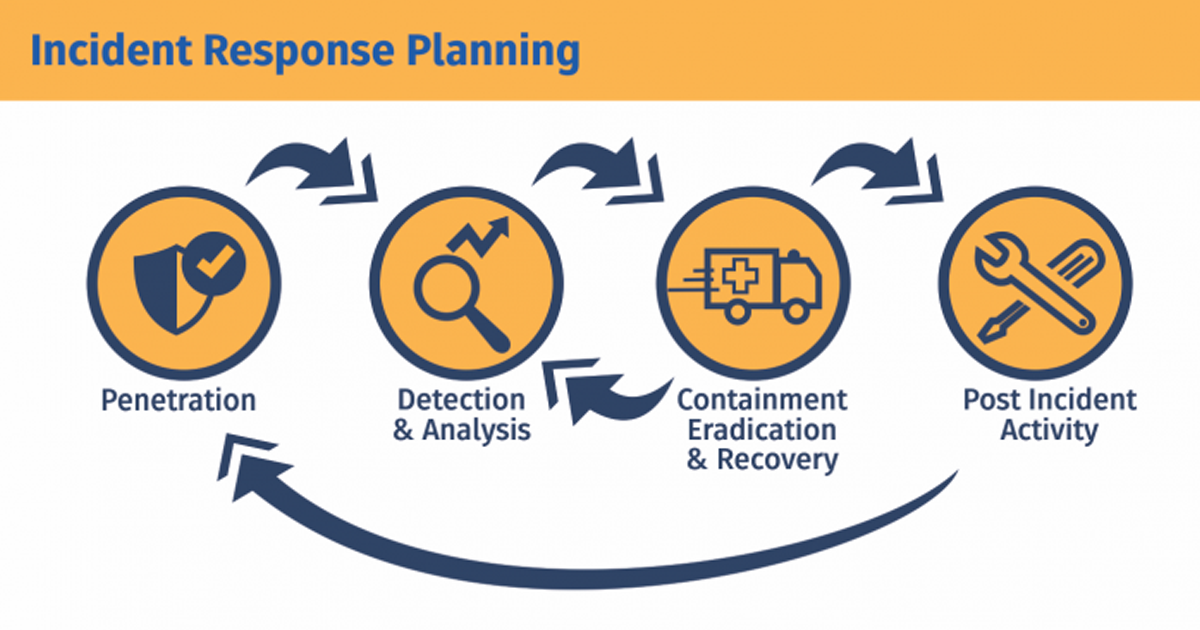
Incident Response (IR) is a structured approach to handling and managing security incidents and data breaches. The primary goal of incident response is to minimize the impact of an incident and reduce the time it takes to identify and respond to security threats. Key aspects of Incident Response include:
Preparation: Develop an Incident Response Plan (IRP) outlining the roles, responsibilities, and procedures for handling incidents. This plan should be regularly tested and updated.
Identification: Detect and identify security incidents through various means, such as intrusion detection systems, log analysis, and user reports.
Containment: Isolate affected systems and networks to prevent further spread of the incident.
Eradication: Identify and eliminate the root cause of the incident to prevent future occurrences.
Recovery: Restore affected systems and data to their normal state.
Lessons Learned: Conduct a post-incident analysis to identify areas for improvement and update the IRP based on lessons learned.
Coordination: Collaborate with relevant stakeholders, including IT teams, legal, management, and law enforcement (if necessary), throughout the incident response process.
Malware Analysis:
Malware analysis is the process of dissecting and examining malicious software (malware) to understand its behaviour, functionality, and potential impact on systems and data. The primary goal of malware analysis is to develop effective countermeasures and prevent further infections. Key aspects of Malware Analysis include:
Static Analysis: Involves examining the code and structure of the malware without executing it. This analysis can provide insights into the malware's functionality and potential indicators of compromise.
Dynamic Analysis: Involves executing the malware in a controlled environment (sandbox) to observe its behaviour, such as network communication, file modifications, and process interactions.
Behavioural Analysis: Focuses on understanding the malware's actions and capabilities once it infects a system, including data theft, privilege escalation, or botnet participation.
Reverse Engineering: Involves disassembling the malware to understand its code, logic, and algorithms.
Indicators of Compromise (IOCs): Identifying IOCs, such as file hashes, IP addresses, or patterns in the malware's behaviour, to help detect and block similar threats in the future.
Threat Intelligence: Leveraging threat intelligence sources to contextualize and identify the malware's origin and potential threat actor groups.
Both Incident Response and Malware Analysis play critical roles in responding to and mitigating cyber threats. By promptly and effectively handling security incidents and understanding the behaviour of malware, organizations can better protect their systems, data, and reputation. Integration of Incident Response and Malware Analysis into the cybersecurity strategy can significantly enhance an organization's overall resilience against cyber threats.
